#ldap group
Explore tagged Tumblr posts
Text
so a month ago I spun up a new production environment and turned it into a 1-1 clone of an existing one, just with a different name. i could sign in, my boss could sign in. great, time to fuck off and hand it over to the user group.
last week users try to get it and they can't. weird, what the fuck? I can get in, my boss can still get in, why cant they? I remigrate the configuration files and have them try it again, users still can't authenticate.
i bring in my technical rep, we troubleshoot ldap settings, users still can't get in. we build new configurations from scratch, users still can't get in.
we bring in tier 2 technical reps, they ask us to list all users in the new environment:
username | role | last login
no users found.
I can still sign in, my boss can still sign in, but no users exist at all in the environment. we hand copy all of the users from the old environment to the new and suddenly everyone can authenticate.
how the fuck could my boss and I log in????? I could understand if I was using the generic user account I created upon environment initialization, I believe I named it something like AssFarts with a password Hunter2, but no, I was signing into an account that didnt exist.
11 notes
·
View notes
Text
Future-Proof Your IT Career with TechshilaMind’s Active Directory Administrator Course
In today’s enterprise environments, managing users, securing data, and controlling access are mission-critical responsibilities. If you're looking to become an essential part of any organization's IT backbone, Active Directory (AD) mastery is non-negotiable.
At TechshilaMind, the Active Directory Administrator course is crafted by experts to ensure you're ready to lead in these areas with confidence and skill.
What is Active Directory? Why Should You Learn It?
Active Directory is Microsoft's identity and access management service used by 90%+ of Fortune 1000 companies. It serves as a centralized system for:
User Authentication
Network Resource Management
Security Policy Enforcement
Learning AD helps you understand the core of enterprise-level infrastructure and positions you as a valuable asset in roles such as:
System Administrator
Network Administrator
IT Support Engineer
Security Analyst
Explore how this technology can elevate your IT skill set in the Active Directory Administrator course.
In-Depth Course Curriculum Highlights
The course is structured to ensure clarity and progression – from basic to expert-level competencies:
Module 1: Introduction to Active Directory
What is AD?
Architecture and Components
AD vs Azure AD
Module 2: Setting Up Domain Controllers
Installing and Configuring ADDS
DNS Integration
Creating Domains and Forests
Module 3: User and Group Management
OU (Organizational Unit) Structure
Managing Users, Groups, and Computers
Scripting with PowerShell
Module 4: Group Policy Objects (GPOs)
What are GPOs?
Creating and Linking GPOs
Group Policy Troubleshooting
Module 5: Security, Backup, and Recovery
AD Security Best Practices
Implementing Role-Based Access Control
AD Backup, Restore, and Disaster Recovery
Module 6: Real-Time Case Studies & Project Work
Industry Use Cases
Hands-On Assignments
Simulated Scenarios
Download the full syllabus by visiting the course page.
Who Should Join This Course?
Whether you're starting from scratch or polishing your skills, this course suits:
Fresh IT graduates seeking a powerful niche
System Admins upgrading their skillset
Cybersecurity professionals needing infrastructure knowledge
Tech leads and managers exploring AD deployment at scale
Key Features That Set This Course Apart
✅ Live Instructor-Led Sessions ✅ 24/7 Dedicated Mentor Support ✅ Interview Prep + Career Mentorship ✅ Flexible Weekday & Weekend Schedules ✅ Access to LMS + Recorded Lectures ✅ Official Certification Preparation
What You Can Expect After Completion
Job-Ready Skills to handle Active Directory infrastructure
Certification-ready preparation for roles such as MCSA, Microsoft Certified: Azure Administrator Associate
Boosted Employability with in-demand tools like PowerShell, GPO, LDAP
Get started now: Join the Active Directory Administrator course today
Still Have Questions?
Contact TechshilaMind directly for a free consultation:
📞 +91-7505974183
What Students Are Saying
⭐⭐⭐⭐⭐ “The instructors are highly knowledgeable, and I loved how real-time projects were part of the learning. Definitely worth the investment!” — Amit Sharma, Network Engineer
⭐⭐⭐⭐ “Perfect for those trying to break into infrastructure roles. Their career support was the cherry on top.” — Nisha R., System Admin Intern
Your Path to Becoming an AD Expert Starts Here
If you've been looking for a well-structured, job-oriented course that delivers not just knowledge but career impact, then the Active Directory Administrator course from TechshilaMind is your launchpad.
0 notes
Text
SAP HANA
SAP HANA includes robust security measures to ensure data protection, system integrity, and compliance with industry standards. Here’s a breakdown of the key security features built into SAP HANA:
1. User and Role Management
Authentication: Supports multiple authentication methods, including:Username and passwordKerberosSecurity Assertion Markup Language (SAML)X.509 client certificates
Authorization: Granular role-based access control (RBAC) allows defining permissions at the object and system levels.
User Groups: Logical grouping of users simplifies the management of permissions and roles.
2. Data Encryption
In-Memory Data Encryption: Sensitive data stored in memory is encrypted to prevent unauthorized access.
Data-at-Rest Encryption: SAP HANA encrypts database volumes and backups using AES-256 encryption.
Data-in-Transit Encryption: Uses TLS/SSL to secure communication channels between clients, applications, and the SAP HANA server.
3. Secure Network Communication
Encryption Protocols: TLS/SSL ensures secure communication between SAP HANA and external systems.
Firewall Integration: Network security policies can restrict unauthorized connections.
4. Auditing and Logging
Audit Logging: Tracks user activities, system access, and configuration changes for monitoring and compliance.
Change Logs: Records all changes made to database objects and configurations.
Alert System: Real-time alerts for suspicious activities or anomalies.
5. System and Application Security
Secure Configuration: SAP HANA includes a built-in Security Administration Console to manage system settings and ensure a secure configuration.
Patch Management: Regular updates and patches address vulnerabilities promptly.
Application Privileges: Applications running on SAP HANA are restricted by specific privileges to prevent unauthorized access to system resources.
6. Data Masking and Anonymization
Dynamic Data Masking: Masks sensitive data in queries based on user roles.
Data Anonymization: Ensures compliance with data privacy regulations by anonymizing data for non-authorized users.
7. Multi-Tenant Database Security
Isolation: Each tenant database in a multi-tenant SAP HANA system is securely isolated from others.
Separate Roles and Permissions: Unique administrative and user roles for each tenant.
8. Advanced Security Features
Native Integration with Identity Providers: Integrates with third-party identity management systems like Active Directory or LDAP.
Secure Backup and Recovery: Ensures encrypted backups and controlled recovery processes to maintain data integrity.
Anti-SQL Injection: Built-in query validation to prevent injection attacks.
9. Compliance and Standards
Certifications: SAP HANA complies with industry standards like ISO/IEC 27001, SOC 2, and GDPR.
Data Privacy: Supports features like data anonymization, data masking, and data retention to comply with privacy laws.
Audit Readiness: Provides comprehensive logging and reporting tools to meet audit requirements.
10. Threat Detection and Mitigation
Intrusion Detection: Monitors for unusual activities and potential security breaches.
SAP Enterprise Threat Detection: Works with SAP HANA to provide real-time insights into potential threats.
Sandboxing: Restricts the execution of untrusted code within secure environments.
Summary:
SAP HANA’s security framework is built around comprehensive user access controls, robust encryption mechanisms, and proactive monitoring to safeguard data and systems. These features ensure compliance with global standards and provide a secure environment for enterprise operations.
Anubhav Trainings is an SAP training provider that offers various SAP courses, including SAP UI5 training. Their SAP Ui5 training program covers various topics, including warehouse structure and organization, goods receipt and issue, internal warehouse movements, inventory management, physical inventory, and much more.
Call us on +91-84484 54549
Mail us on [email protected]
Website: Anubhav Online Trainings | UI5, Fiori, S/4HANA Trainings

0 notes
Link
1 note
·
View note
Text
Self-Hosted Messengers: The Future of Secure Team Collaboration
You need a self-hosted server to host your enterprise work conversations!
Indeed, self-hosted messenger the only way you bring your teams together to exchange work ideas and discuss more work.
Making your teams rely on personal chat applications at your workplace is no fun when you seriously look for productive outcomes from them you must provide self-hosting chat applications. Instead, give them the best self hosted chat software like Troop Messenger, Flock, Rocket Chat, Mattermost, etc., to stay informed and monitor all the work routines and updates.
These days, business entities, corporates, startups, SMEs, large enterprises, etc., are bombarded with many collaboration tool options. And, most of the tools are available in the variants of SaaS and Self-Hosting.

While data is essential to all industries, government agencies and large corporations place a high premium on enterprise risk management. Therefore, for these kinds of data-specific companies, an instant messaging solution that offers on-premise chat is advised. Let's examine the following business collaboration solutions that provide chat room software and meet these organisations' internal communication needs.

Data-sensitive and regulated businesses such as Governments, Defense, Large Enterprises, Manufacturing, Pharma, etc., need a secured chat platform, unlike web-based chat software for their internal office communication to collaborate without compromising on the data they communicate. The self-hosted chat server Troop GRIT is powered by Troop Messenger's chat engine. They have complete control over the program thanks to this self-hosted messenger since they may direct talks through their databases and networks.
You can get a customized version of hosted messaging to suit the operations of your ecosystem. As this self-hosted chat software supports Air-Gapped Networks, you can be assured of not having any third-party intrusion to access your standard or critical data.
The Deployment suite for Linux and Windows help you with detailed instruction to set it up on your on-premise servers with detailed documentation. This on-premise chat application guides you on the prerequisites for operating systems, databases, and server specifications. This self-hosting chat application will help you on; how to install docker, register, and configure SSL certificate and firewall policies.
Besides providing all the standard and productive features of SaaS, Troop Messenger, the self-managed office chat messenger, comes with Trumpet, File Deck, TM-Monitor (with Lawful Interception), UNITs, User Authorization, etc., as advanced features. End-to-end encryption, Multi-factor authentication, LDAP/SSO, and Role-Based access controls are the exclusive features for user security.
Pros
Comprehensive File Management System-File Deck
End-to-End Encryption
Feature-access controls
Trial License
Guest User-Orange Member
Impressive UI with immersive UX
2. MirrorFly
MirrorFly is an in-app communication provider that is popularly known for its feature-rich video, voice, and chat SDKs. This self-hosted chat software offers a wide range of team communication features, including real-time group chat, HQ audio, and HD video calls, file sharing, moderation, presence indicators, push notifications, and user analytics. Businesses of any scale and size can build their white-label web and mobile apps with its 150+ customizable features and deploy apps on their own premise.
When it comes to protecting user data and privacy, MirrorFly ensures that team conversations are protected end-to-end with built-in security protocols like AES-256 and SSL, along with industry-grade privacy regulations. Above this, users can flexibly deploy their apps on their own premises or on MirrorFly’s dedicated cloud servers, for maximum security, performance, and server maintenance.
Pros
Provides fully customizable video, voice, and chat features
MirrorFly Chat SDKs are available for a lifetime FREE access
Offers complete white-label solution
Let developers hire a complete dedicated team for full integration support
Provides End-to-End security encryption
Cons
MirrorFly currently does not support the recording of ongoing video sessions
Do not provide options to create meeting agendas
Pricing
MirrorFly adapts a twin pricing model - SaaS and SaaP solutions, tailor-made to suit different business needs. The self-hosting solution permits users 100% customization just for a one-time license cost. On the other hand, the cloud-based pricing model comes with 3 monthly plans - Easy (completely FREE), Essentials (starting at $399), and Premium (starting at $999).
3. Wickr
Wickr, an encrypted messaging app, has been acquired by Amazon and is now part of the Amazon Web Services-AWS team. It supports the deployment models of Federated SaaS and On-Premise. This self-hosted messenger is made to serve its customers and partners with its modern collaboration features such as messaging, voice-video calling, file sharing, and others.
Due to the Covid-19 pandemic, the rise of the hybrid work environment has skyrocketed and, the exchange of organizational data between different networks could be a big security threat. With an on-premise chat server like Wickr, all the messages, calls, and files that travel across various devices will be rightly encapsulated and secured.
Pros
This self-hosted chat server provides the client-side E2E encryption
Easy to set-up
You can get started with its free plan
Centralized messaging archived capability
Cons
Limited features in the free plan and the paid plans seem to be expensive.
The code is available on Github, but it’s not open-source
Pricing
Wickr offers a free plan for individuals and small teams with up to 10 registered users. The other paid plan includes Silver at $4.99/user/month, Gold at $9.99/user/month, and Platinum at $25.00/user/month.
4. Element | Secure collaboration and messaging
Element | Secure collaboration and messaging is been built on Matrix and it is considered the best open-source chat server. It offers personal messaging and enterprise collaboration to provide independent and secure communication. It allows users to bring their WhatsApp, Signal, and Telegram chats into its personal messaging variant, Element One. This open-source enterprise collaboration tool provides end-to-end encryption for your messages along with unlimited audio and video.
The primary advantage of the self hosted messenger is, that you can be the owner of your data, which means you can store your messages on your end. Enterprises can choose between "hosted by us" in the Element cloud or on-premise deployment models to securely run their work conversations. This self-hosted chat platform provides you with different kinds of rooms, such as private, internal, and public.
Pros
Fully managed to host with integrations and bridging facilities
Made for personal messaging, enterprise collaboration, and communities too
Open-source software and shares the code with everyone
Cost-Effective
Cons
Its desktop app from the SaaS edition should be a little more intuitive
Occasional bugs in its mobile app, but they are manageable
Pricing
To get started with Element, the pricing model starts from $ 3 per user/per month. The other products, such as Element One and Element Enterprise are charged $5 per month for one user and $4 per monthly active user, respectively. It also helps you bridge your existing communication at $0.50 per remote monthly active user.
5. Rocket.Chat
Rocket.Chat is famously known for its open-source team communication. The two delivery models that are available with this tool are; SaaS and Self-Managed. Large Enterprises can hugely benefit from this hosted chat service as it extends high security to message exchanges with two-factor authentication, E2E encryption, SSO, and OAuth providers. An exclusive feature of real-time translation in this free chat software for businesses translates its UI to over 50 languages making users feel native. The self-managed version allows users to download the docker image and install the application on their servers.
Pros
It has an unlimited free plan
It supports endless customizations that include; Integrations, Plugins, Themes, and Powerful APIs
Easy-to-implement data importers
Scale as per your needs
Open source group chat
Cons
Lack of in-depth documentation
Need better support and sales system
Pricing
Rocket Chat provides different pricing structures for Self-Managed and Cloud. For Self-Managed, it has come up with the pricing plans of Community @ Free, Pro @ $3/per user/month, and Enterprise @ Tiered pricing. The Bronze, Silver, and Gold pricing plans of the Cloud/SaaS delivery model come at $2/user/month, $4/user/month, and tiered pricing respectively.
6. Mattermost
Mattermost is the best open-source chat software that introduces itself as a ‘High Trust Messaging for the Enterprise, and it is true. An exceptional self-hosted open-source messaging platform that extends secure communication across industries of all forms and sizes. This private chat software can be deployed on a private cloud within the premises of local servers. Organizations that are highly privacy-conscious believe Mattermost as their flexible partner for all internal instant communications. The tool is popular on GitHub, and it provides an extensive level of documentation that helps in docker installation.
Pros
Build custom workflows
Enables Dev Ops workflows
Enterprise-grade scalability and security
Supports Migration
Cons
Tedious deployment process
No in-app voice-video call feature. Need to integrate.
Pricing
Mattermost comes with two delivery models; cloud and self-hosted. Large Enterprises who are looking for self-hosting can go with a server download that supports both Linux Install and Docker installation. Moving forward, it extends the free 30-day trial of Enterprise Edition(E20). And, the other plans E10 and E20 are priced at $3.25 per user/month and $8.50 per user/month when billed annually.
7. Zulip
Catching up on only important conversations and ignoring irrelevant ones, is what Zulip says. Open-source software was built by hundreds of developers across the globe. The self-hosted delivery model specifically designed for Large Entities provides an excellent production installation guide that lets users deploy it on their networks. Besides its 90 native integrations, this self-hosted corporate messenger supports more integrations from Hubot, Zapier, and IFTTT. This self-hosted chat app provides excellent user documentation ranging from product installation guides to stream management.
Pros
It has high-quality developer-friendly code.
Build your integrations with its APIs
Unique threading approach
Open-source team chat
Supports migration
Cons
Steep learning curve
Minimalistic features
Pricing
Zulip Cloud and Zulip On-Premise are two different pricing models that it offers. The former comes with Free and Standard Plans at unlimited and $6.67/user/month respectively, and the latter comes with the plans of Community Support as Free and Open source forever. The Enterprise pricing variant of the same varies with the support required. Users need to contact their sales team.
8. Matrix.org
Besides a messaging protocol, Matrix is known as a decentralized conversation store. It replicates the sent message over all the servers where user participation is active. An exceptional self-hosted delivery model that provides strong end-to-end encryption via the Olm and Megolm cryptographic ratchets. This self-hosted instant messenger helps to build your apps, chat rooms, direct chats, and chatbots, with simple RESTful HTTP/JSON APIs.
Pros
Each server has full-level control over users' data.
Open specification of Matrix standard
No single point of control or failure
Supports Bridging
Cons
Not available on the cloud
Pricing
Matrix.org never charges. It's completely free. Its free servers are open to all for public registrations.
9. Lets Chat
Yours is a small team and want to have full-scale control over your team collaboration. Then Let's Chat is the right self-hosted tool exclusively made for small teams. It runs on Node.js and MongoDB and is deployed easily on your local servers. It supports Docker and Vagrant platform installations. This self-hosted chat server has some interesting features; private/password-protected rooms, Image embeds, transcripts/chat history, and more.
Pros
Supports LDAP/Kerberos Authentication
Supports BYOS (Bring your own server)
It has multiple chat rooms
It is Hubot-friendly
Cons
Not available over the cloud
It doesn’t support any integrations.
Pricing
It’s free(MIT Licensed)
10. Nextcloud
The self-hosted collaboration tool built for protecting user data through multiple layers of security offers a wide range of products like Nextcloud Files, Nextcloud Talk, Nextcloud Groupware, Nextcloud at home, and industry solutions. Nextcloud says, ‘control is key to data’. To ensure this, it implements the authentication mechanisms of SAML, Kerberos, and LDAP. It’s an open-source application with code available on GitHub for developers.
Pros
It has two variants; Nextcloud at home and Nextcloud at Enterprise.
Adhere to the compliances of HIPPA and GDPR
Enterprise support
Direct access to core Nextcloud Engineering.
Cons
Has fewer issues with deployment on shared hosting
No detailed manual installation guides.
Pricing
Nextcloud offers three pricing plans; Basic, Standard, and Premium. The annual pricing for Basic, Standard, and Premium for 50 users is priced at 1900 euros, 3400 euros, and 4900 euros respectively.
0 notes
Text
Security in OpenShift
OpenShift is designed with security in mind, providing numerous features and practices to ensure your applications and data are protected. This blog post will cover the security features and practices, how to manage roles and permissions, and best practices for securing your OpenShift environment.
Security Features and Practices
1. Integrated Security Controls:
Pod Security Policies (PSPs): Enforce security contexts for pods, ensuring they run with the least privilege required.
Network Policies: Control the traffic flow between pods using network policies to isolate applications and restrict communication to only what is necessary.
Service Mesh: Use Istio service mesh for advanced traffic management, security, and observability.
2. Identity and Access Management:
OAuth Integration: Integrate with various OAuth providers for authentication.
User Authentication: Support for multiple authentication methods, including LDAP, GitHub, GitLab, and more.
Multi-Factor Authentication (MFA): Enhance security by requiring multiple forms of verification.
3. Data Security:
Encryption: Encrypt data at rest and in transit using TLS and other encryption protocols.
Persistent Volume Encryption: Ensure that data stored in persistent volumes is encrypted.
Secret Management: Securely store sensitive information like API keys and passwords using OpenShift secrets.
4. Compliance and Auditing:
Audit Logs: Maintain detailed logs of user and system activities to meet compliance requirements and for forensic analysis.
Policy Enforcement: Use Open Policy Agent (OPA) for fine-grained policy control.
Managing Roles and Permissions
1. Role-Based Access Control (RBAC):
Roles and RoleBindings: Define roles with specific permissions and bind them to users or groups.
ClusterRoles and ClusterRoleBindings: Manage permissions at the cluster level.
2. Creating Roles:
Custom Roles: Create custom roles tailored to your specific needs.
kind: Role
apiVersion: rbac.authorization.k8s.io/v1
metadata:
namespace: mynamespace
name: mycustomrole
rules:
- apiGroups: [""]
resources: ["pods"]
verbs: ["get", "list", "watch"]
3. Assigning Roles:
RoleBinding Example:
kind: RoleBinding
apiVersion: rbac.authorization.k8s.io/v1
metadata:
name: myrolebinding
namespace: mynamespace
subjects:
- kind: User
name: myuser
roleRef:
kind: Role
name: mycustomrole
apiGroup: rbac.authorization.k8s.io
4. Managing Cluster-Wide Permissions:
Use ClusterRoles and ClusterRoleBindings for permissions that need to be applied across the entire cluster.
Best Practices for Securing Your OpenShift Environment
1. Principle of Least Privilege:
Assign the minimum necessary permissions to users and services to reduce the attack surface.
2. Regular Audits and Reviews:
Periodically review roles, permissions, and security settings to ensure they are up-to-date and aligned with security policies.
3. Network Segmentation:
Use network policies to segment your network, isolating critical components and limiting the blast radius of potential breaches.
4. Secure CI/CD Pipelines:
Implement security checks in your CI/CD pipelines to detect vulnerabilities early.
Use image scanning tools to ensure that container images are free of known vulnerabilities.
5. Monitor and Respond:
Continuously monitor your environment using tools like Prometheus and Grafana.
Set up alerting mechanisms for suspicious activities and potential security incidents.
6. Keep OpenShift Updated:
Regularly update OpenShift and its components to the latest versions to benefit from security patches and improvements.
7. Secure API Access:
Use API server auditing and limit API access to trusted sources only.
Implement rate limiting to prevent abuse.
Conclusion
Securing your OpenShift environment requires a comprehensive approach that includes integrated security controls, proper management of roles and permissions, and adherence to best practices. By following the guidelines and recommendations outlined in this post, you can create a robust security posture for your OpenShift deployments.
www.hawkstack.com
#redhatcourses#information technology#linux#containerorchestration#docker#kubernetes#container#containersecurity#dockerswarm#aws
0 notes
Text
do you need license for vpn on palo alto
🔒🌍✨ Get 3 Months FREE VPN - Secure & Private Internet Access Worldwide! Click Here ✨🌍🔒
do you need license for vpn on palo alto
VPN licensing Palo Alto
A Virtual Private Network (VPN) is essential for businesses looking to securely connect their remote employees to the company's network. Palo Alto Networks is a renowned provider of security solutions, including VPN services. When it comes to VPN licensing options offered by Palo Alto, there are several factors to consider.
Palo Alto Networks offers VPN licensing based on the number of concurrent users or devices connecting to the VPN. This means that businesses can choose a licensing model that best fits their operational needs. Whether you have a small business with a limited number of remote employees or a large enterprise requiring a scalable VPN solution, Palo Alto Networks has licensing options to accommodate your requirements.
Palo Alto's VPN licensing also includes additional features such as advanced security functionalities, user authentication mechanisms, and integration capabilities with other security tools. This ensures that your VPN connection is not only secure but also optimized for performance and user experience.
By investing in Palo Alto's VPN licensing, businesses can benefit from top-tier security protocols, centralized management, and robust support services. This translates to a reliable and secure VPN infrastructure that protects your sensitive data and network resources from cyber threats.
In conclusion, Palo Alto Networks' VPN licensing offers businesses the flexibility, scalability, and security needed to establish a reliable and secure VPN connection for their remote workforce. Whether you are a small business or a large enterprise, Palo Alto's VPN licensing options can cater to your specific requirements and enhance your network security posture.
Palo Alto VPN requirements
Title: Understanding Palo Alto VPN Requirements
In the digital age, ensuring secure connectivity for remote workers and branch offices is paramount. Palo Alto Networks, a leading cybersecurity company, offers robust VPN (Virtual Private Network) solutions designed to meet the evolving needs of modern enterprises. However, before implementing a Palo Alto VPN, it's crucial to understand the requirements involved to ensure seamless integration and maximum security.
Compatible Hardware: Palo Alto VPN solutions require compatible hardware, such as Palo Alto Network firewalls or VPN gateways. These devices play a pivotal role in establishing secure connections and enforcing access policies.
License and Software Version: A valid license for the Palo Alto VPN feature is essential. Additionally, it's imperative to ensure that the firewall or gateway is running a supported software version compatible with the VPN functionality.
Network Infrastructure: The effectiveness of a VPN relies heavily on the underlying network infrastructure. Organizations must have a stable internet connection with sufficient bandwidth to accommodate VPN traffic without compromising performance.
Authentication Mechanisms: Palo Alto VPNs support various authentication mechanisms, including pre-shared keys, digital certificates, and integration with external authentication services like LDAP or RADIUS. Administrators need to configure authentication methods based on security policies and user requirements.
Encryption and Tunneling Protocols: Palo Alto VPNs support industry-standard encryption and tunneling protocols such as IPsec (Internet Protocol Security) and SSL/TLS (Secure Socket Layer/Transport Layer Security). Selecting appropriate encryption algorithms and key strengths is crucial to maintaining data confidentiality and integrity.
Access Control Policies: Granular access control policies should be defined to regulate VPN usage and restrict unauthorized access to sensitive resources. This involves configuring firewall rules, VPN profiles, and user/group-based access policies according to organizational security guidelines.
By adhering to these requirements, organizations can deploy Palo Alto VPNs effectively to safeguard their networks and ensure secure remote access for employees and partners. With robust encryption, centralized management, and advanced threat prevention capabilities, Palo Alto VPN solutions offer a comprehensive approach to network security in today's dynamic business landscape.
Licensing for Palo Alto VPN
When utilizing Palo Alto VPN services, having a clear understanding of licensing is crucial. Palo Alto Networks offers various licensing options tailored to meet different business needs.
The Palo Alto VPN licensing model typically includes subscriptions for different features and services. These subscriptions may encompass functionalities such as next-generation firewall security, threat prevention, URL filtering, GlobalProtect VPN, WildFire malware analysis, and more.
One of the commonly used licensing models for Palo Alto VPN is based on the number of concurrent users or devices. This model allows organizations to scale their VPN connectivity based on their requirements, paying for the number of simultaneous VPN connections needed.
Moreover, Palo Alto Networks may offer licensing options based on the duration of the subscription, such as annual or multi-year plans. These plans often come with additional support services, software updates, and access to threat intelligence to ensure the VPN infrastructure remains secure and up to date.
Understanding the licensing for Palo Alto VPN is essential for businesses to ensure they have the appropriate features and support needed to maintain secure remote access for their users. By choosing the right licensing model and subscription plan, organizations can effectively leverage Palo Alto VPN services to enhance their network security posture.
Palo Alto VPN license necessity
In today's increasingly interconnected digital landscape, ensuring the security and privacy of online communications is paramount. For individuals and businesses alike, utilizing Virtual Private Network (VPN) technology has become a common practice to safeguard sensitive data from prying eyes and malicious actors. One prominent player in the VPN market is Palo Alto Networks, renowned for its robust security solutions. However, the question arises: Is a Palo Alto VPN license a necessity?
The answer largely depends on the specific requirements and security objectives of the user. Palo Alto VPN licenses offer a range of features and functionalities tailored to meet diverse needs, including advanced encryption protocols, secure remote access capabilities, and comprehensive threat prevention mechanisms. For organizations handling sensitive information or operating in regulated industries, such as finance or healthcare, investing in a Palo Alto VPN license can be crucial for maintaining compliance with data protection regulations and safeguarding against potential cyber threats.
Moreover, Palo Alto VPN licenses often come bundled with additional security services and support options, providing users with peace of mind and ongoing assistance in managing their network security infrastructure. From real-time threat intelligence updates to proactive security monitoring and incident response, these added benefits can significantly enhance the overall effectiveness and resilience of an organization's cybersecurity posture.
Furthermore, in today's remote work environment where employees frequently access corporate networks from various locations and devices, deploying a Palo Alto VPN solution ensures secure connectivity and seamless access to critical resources without compromising data integrity or confidentiality. By encrypting all communication channels and enforcing strict access controls, Palo Alto VPNs help mitigate the risk of unauthorized access and data breaches, thereby bolstering the overall resilience of the organization's IT infrastructure.
In conclusion, while the necessity of a Palo Alto VPN license may vary depending on individual circumstances, its value in enhancing cybersecurity and safeguarding sensitive data cannot be overstated. For organizations prioritizing security and compliance, investing in a Palo Alto VPN license is a prudent decision that pays dividends in terms of risk mitigation, regulatory adherence, and peace of mind.
VPN license on Palo Alto firewall
A VPN license on a Palo Alto firewall is essential for ensuring secure and encrypted communications over virtual private networks. Palo Alto Networks offers different types of VPN licenses to cater to various business needs and requirements. These licenses enable organizations to establish secure connections between remote locations, cloud infrastructures, and mobile users.
By obtaining a VPN license on a Palo Alto firewall, businesses can enhance their network security and protect sensitive data from unauthorized access or cyber threats. These licenses provide advanced features such as strong encryption, secure tunneling protocols, and multi-factor authentication to ensure the confidentiality, integrity, and availability of data transmitted over VPN connections.
One of the key benefits of a VPN license on a Palo Alto firewall is the ability to establish site-to-site VPN connections, allowing different branch offices or remote locations to securely communicate with each other over the internet. This facilitates seamless collaboration and data sharing between geographically dispersed teams without compromising security.
Furthermore, VPN licenses on Palo Alto firewalls offer scalability and flexibility, enabling businesses to easily expand their VPN infrastructure as their network requirements evolve. With robust security capabilities and centralized management, Palo Alto firewalls with VPN licenses provide a comprehensive solution for organizations looking to establish secure and reliable connectivity across their network.
In conclusion, investing in a VPN license on a Palo Alto firewall is a prudent decision for organizations seeking to bolster their network security and establish encrypted communication channels. By leveraging the advanced features and capabilities of Palo Alto firewalls, businesses can mitigate cybersecurity risks and safeguard their critical assets from potential threats in today's digital landscape.
0 notes
Text
TerraMaster F4-424 Pro: The Most Powerful 4-Bay NAS

TerraMaster F4-424 Pro Developed to Meet High Performance Needs
For SMB users who require high-performance storage solutions, the 4-Bay TerraMaster F4-424 Pro is a good choice. High performance enables users to manage workloads with ease, and multiple business-level backup options ensure data security and reduce the possibility of data loss.
The Strongest 4-Bay NAS The most potent 4-bay NAS available today is the TerraMaster F4-424 Pro. It has an integrated Intel UHD Graphics card with a maximum dynamic frequency of 1.25GHz, an Intel Core i3 8-core, 8-thread processor with a maximum turbo frequency of 3.8GHz, and hardware encryption support for AES NI. The disc array’s storage efficiency is greatly increased by its 32GB DDR5 4800MHz memory, two 2.5G Ethernet ports, and integrated dual M.2 NVMe slots for SSD caching. This makes the TerraMaster F4-424 Pro a great high-performance storage option for users running database applications and virtualization in small and medium-sized businesses.
Quicker Application Reaction With its DDR5 memory and more potent CPU, the TerraMaster F4-424 Pro offers a performance boost over 150% over its predecessor. Application load times have increased by 100%, file and photo retrieval speed has increased by 45%, database response speed has increased by 55%, and web page PHP response has improved by an astounding 65%. High-load workflows can be handled with ease thanks to this improved performance.
Faster Transmission Rate With two 2.5 GbE interfaces installed, the TerraMaster F4-424 Pro can support a high-speed network bandwidth of 2.5 GbE. 283 MB/s is the maximum linear data transmission speed (Seagate IronWolf 18TB x 4, RAID 0). Link Aggregation is a cost-effective solution for multi-user, high-concurrent file access because it provides a network bandwidth of up to 5 Gb.
Strong Multimedia Provider In order to provide users with consistent, dependable entertainment, the TerraMaster F4-424 Pro, equipped with 4K video decoding capabilities, is compatible with the uPnP/DLNA protocol and can stream videos to a variety of multimedia devices, such as computers, smartphones, media players, and televisions, through the use of TerraMaster’s in-house application Multimedia Server or one from a third party.
Adaptable Storage Setup Multiple RAID types, including Single/RAID 0/1/5/6/10, are supported by the TerraMaster F4-424 Pro. It provides online migration and capacity expansion for various RAID types. The disc array can be set up for Hot Spare. Multiple storage spaces can be created with it, and BTRFS or ext 4 file systems can be chosen based on different business needs. Storage capacity can be expanded flexibly with the F4-424 Pro when used in conjunction with TerraMaster USB DAS devices.
Expert Operating System The TerraMaster operating system, TOS, was created based on Linux and powers TNAS.Professional storage management functions like network management, permission management, storage management, and resource monitoring can be integrated via user-friendly, intuitive, and flat web interfaces. thanks to extensive research into the needs of various business users and the subsequent continued evolution of multiple TOS generations. Additionally, it offers hundreds of free apps on the app store.
File Services Across Platforms The TerraMaster F4-424 Pro can effectively handle the cross-platform file service requirements of various network environments because it supports the majority of file services, including SMB, AFP, SFTP/FTP, iSCSI, NFS, and WebDAV. Additionally, the TerraMaster F4-424 Pro supports LDAP and the Windows AD domain, which makes it easier to integrate business users’ current IT environments and boosts management effectiveness. The F4-424 Pro can meet business users’ extensive needs for data security and interdepartmental collaboration because it has permission management at the user, user group, and file directory levels.
TerraMaster F4 Comprehensive Backup Options
Because TOS integrates with multiple backup applications that can handle backup needs in a variety of circumstances, it can protect valuable data with visual user interfaces and reliable storage solutions.
Centralised Backup Data can be quickly restored following incidents when backups are started at the TNAS end for servers,virtual machines, staff PCs, and file servers.
Duple Backup Duple Backup offers enhanced data protection by backing up files to a different remote TNAS, file server, or cloud drive in order to provide multiple offsite backup versions.
Snapshot With the advanced storage technology and optimised snapshot technology made available by the BTRFS file system, you can enable the snapshot schedule to take continuous snapshots of your folders or iSCSI LUNs. Your data is well protected because the system can restore to the most recent backup and roll back to specific points in time when issues occur.
Cloud Sync This synchronises or backs up TNAS data with the cloud drive, increasing cloud data availability and providing multiple offsite backup copies to protect your data security.
Applications in Virtualized Environments By utilising professional virtualized applications like VirtualBox and Docker and collaborating with Docker-compose and Portainer, the TerraMaster F4-424 Pro meets the demands of virtualized applications and offers extra functionality all within one device. As a result, corporate IT investment costs are reduced.
Protection of System Level Security The system security of network devices security systems must address significant challenges due to an increase in cyberattacks. AES 256 encryption, automatic account lockout, firewall, anti-DoS attack, and pam identity authentication are just a few of the systemic protections that TOS makes possible. As a result, it successfully lowers the likelihood that your devices may be attacked by malware.
Various Commercial Uses Business users can quickly and easily create file servers, mail servers, web servers, FTP servers, MySQL databases, CRM, Node.js, Java virtual machines, and many other services with TNAS, meeting the needs of numerous SMBs in industries like finance, education, consulting, scientific research, and law.
Replace Hard Drives More Easily Because of its tool-free hard disc tray design, the TerraMaster F4-424 Pro eliminates the need for any tools when installing hard drives. Additionally, the TerraMaster F4-424 Pro has TerraMaster’s exclusive Push-Lock design, which locks the hard drive automatically upon insertion to stop it from falling out or becoming offline. Because they install in less than ten seconds, this makes it very convenient for users who need to replace hard discs frequently for data exchange.
M.2 SSD Installation Made Easy TerraMaster has specifically designed a side sliding cover for the TerraMaster F4-424 Pro chassis that can be pushed aside to install M.2 SSDs, making the installation process easier. Additionally, TerraMaster offers hand-tightened screws, which facilitate an SSD installation in just five seconds.
Improved Dissipation of Heat The intelligent temperature-controlled fan of the TerraMaster F4-424 Pro maintains ideal operating conditions by automatically modifying fan speed in response to hard disc temperature. For M.2 SSDs, it also features a special ventilation channel designed to support hybrid storage applications. Any M.2 SSD’s temperature can be maintained within a reasonable range even when operating at maximum capacity.
Reduced Noise Because of the unit’s close proximity to the user, it had to be designed to achieve significantly lower noise levels in order to comply with desktop product regulations. When reading or writing, the fast rotation of the discs and heads in HDDs causes audible vibrations. The whole noise may be amplified by these vibrations resonating with the product’s cavity. In order to combat this, Terra Master’s engineers have designed numerous unique sound-absorbing panels in the new structure to minimise noise in addition to adding more shock-absorbing measures. According to testing, the new generation of products achieves 50% lower noise levels than the previous generation, with only 21dB(A) of noise in standby mode!
Test parameters: 1.m test distance; 17.3dB(A) test environment noise; two SATA HDDs/SSDs in standby mode
Stress-free After-Sale Support With its distinctive “provides replacements within 2 years” after-sale policy in place, TerraMaster offers worry-free quality assurance via online customer support in real-time, a technical forum run by professionals, an online user manual, a technical service mailbox, and remote troubleshooting.
Read more on Govindhtech.com
#TerraMasterF4424Pro#ssd#cpu#ddr5#smartphone#inteluhd#linux#virtualmachines#cyberattacks#mysql#Technology#technews#govindhtech
0 notes
Text
can you use asa to connect to cisco anyconnect vpn
🔒🌍✨ Get 3 Months FREE VPN - Secure & Private Internet Access Worldwide! Click Here ✨🌍🔒
can you use asa to connect to cisco anyconnect vpn
ASA Configuration for Cisco AnyConnect VPN
Configuring the Adaptive Security Appliance (ASA) for Cisco AnyConnect VPN provides a secure and reliable way for remote users to connect to the network. By following a few simple steps, network administrators can ensure that the VPN access is properly configured and meets the organization's security requirements.
To begin the configuration process, access the ASA device using the command line interface or through the ASDM (Adaptive Security Device Manager). First, make sure that the ASA has the necessary licensing for AnyConnect VPN connections.
Next, create a group policy that defines the behavior and settings for AnyConnect users. This includes parameters such as DNS servers, split-tunneling policies, and access control settings. Assign this group policy to a tunnel group, which specifies the connection properties for remote users.
Generate and install an SSL certificate on the ASA to secure the VPN connection. This step is crucial to prevent unauthorized access and protect sensitive data transmitted over the VPN.
Configure the AnyConnect VPN profile on the ASA, which includes settings like the VPN server address, authentication methods, and encryption algorithms. Distribute this profile to remote users to enable them to connect to the VPN securely.
Finally, create access control lists (ACLs) to control traffic flow between the VPN users and the internal network. These ACLs help enforce security policies and restrict unauthorized access to sensitive resources.
By following these steps, network administrators can successfully configure the ASA for Cisco AnyConnect VPN, providing secure remote access for users while maintaining the integrity of the network.
Cisco AnyConnect VPN Setup on ASA
Cisco AnyConnect VPN is a popular option for secure remote access to internal networks. Setting up Cisco AnyConnect VPN on the Adaptive Security Appliance (ASA) involves a few key steps to ensure a smooth and secure connection.
Firstly, you need to acquire the appropriate licensing for the number of concurrent VPN connections you require. This can be obtained directly from Cisco or an authorized reseller. Once you have the license, you can proceed with the installation of the AnyConnect software on the ASA.
Next, configure the ASA for VPN access by setting up the necessary policies and access control lists (ACLs). This ensures that only authorized users can establish a VPN connection to the network.
After configuring the ASA, you need to set up user accounts and authentication methods for the VPN users. This can be done locally on the ASA or integrated with an external authentication server such as RADIUS or LDAP for centralized user management.
Once the configuration is complete, users can download the AnyConnect client software from the ASA’s web portal and connect to the VPN using their credentials. The AnyConnect client provides a user-friendly interface for establishing secure VPN connections to the network.
In conclusion, setting up Cisco AnyConnect VPN on ASA involves obtaining the necessary licensing, configuring the ASA, setting up user accounts, and providing users with the AnyConnect client software for secure remote access to the network. By following these steps, you can ensure a secure and efficient VPN setup for your organization.
ASA Firewall Integration with Cisco AnyConnect
Title: Enhancing Network Security: ASA Firewall Integration with Cisco AnyConnect
In today's digital landscape, where cyber threats loom large, safeguarding network infrastructures is paramount for businesses of all sizes. One effective strategy for bolstering security is the integration of Cisco Adaptive Security Appliance (ASA) firewall with Cisco AnyConnect, a versatile VPN client. This integration not only fortifies network defenses but also ensures secure remote access for users, regardless of their location.
ASA firewall serves as a robust barrier against unauthorized access and malicious activities by inspecting and filtering traffic based on predefined security policies. By integrating it with Cisco AnyConnect, organizations can extend this protection to remote users accessing the network from various endpoints.
One of the key benefits of this integration is the establishment of secure VPN connections. Cisco AnyConnect facilitates encrypted communication between remote devices and the ASA firewall, mitigating the risk of data interception or tampering. Additionally, AnyConnect's multi-factor authentication capabilities add an extra layer of security, ensuring that only authorized users can access sensitive resources.
Moreover, the integration enables seamless enforcement of access control policies across the network. Administrators can define granular rules specifying who can access which resources, enhancing security posture without compromising productivity. Furthermore, ASA firewall's advanced threat detection features, such as intrusion prevention and malware protection, complement AnyConnect's capabilities, creating a comprehensive defense mechanism.
Another advantage is simplified management and monitoring. Through centralized management consoles, administrators can oversee VPN connections, configure security policies, and monitor network traffic in real-time, streamlining security operations and facilitating prompt response to potential threats.
In conclusion, integrating ASA firewall with Cisco AnyConnect offers a potent solution for safeguarding network infrastructure and enabling secure remote access. By combining robust firewall protection with advanced VPN capabilities, organizations can mitigate security risks effectively in today's dynamic threat landscape.
Connecting ASA to Cisco AnyConnect VPN
When it comes to secure remote access, connecting the Adaptive Security Appliance (ASA) to Cisco AnyConnect VPN is a popular and effective choice for many organizations. By establishing a connection between these two components, users can securely access the corporate network from remote locations with ease.
To begin the process of connecting ASA to Cisco AnyConnect VPN, the first step is to configure the ASA to support the VPN connection. This includes setting up necessary parameters such as authentication methods, encryption settings, and access control policies. Additionally, the Cisco AnyConnect VPN client software needs to be installed on the devices that will be used for remote access.
Once the ASA is properly configured, users can initiate a VPN connection using the Cisco AnyConnect client. This software provides a user-friendly interface for establishing a secure connection to the ASA, encrypting all data transmitted between the user's device and the corporate network.
Connecting ASA to Cisco AnyConnect VPN offers several benefits, including enhanced security through encryption and authentication mechanisms, as well as flexibility for remote users to access corporate resources from anywhere with an internet connection. This solution is particularly valuable for organizations with remote workers, branch offices, or employees who frequently travel.
In conclusion, connecting ASA to Cisco AnyConnect VPN is a reliable way to enable secure remote access to corporate networks. By following the necessary configuration steps and utilizing the Cisco AnyConnect client software, organizations can ensure that their remote users can securely access company resources while maintaining the confidentiality and integrity of data transmissions.
ASA VPN Configuration for AnyConnect Access
ASA VPN Configuration for AnyConnect Access
Configuring an ASA VPN (Virtual Private Network) for AnyConnect access is vital for secure remote connectivity to corporate networks. Cisco's Adaptive Security Appliance (ASA) offers robust features for establishing VPN connections, ensuring data confidentiality, integrity, and authenticity.
To configure AnyConnect access on an ASA device, follow these steps:
Install AnyConnect Software: Begin by installing the Cisco AnyConnect software on the ASA device. Ensure that you have the appropriate licensing for the number of users and features required.
Enable SSL VPN: Enable Secure Sockets Layer (SSL) VPN on the ASA. SSL VPN provides secure access for remote users through a web browser interface, offering flexibility and ease of use.
Configure Authentication: Set up authentication methods such as local user databases, RADIUS, or LDAP to verify the identities of remote users connecting to the VPN.
Define VPN Group Policies: Create VPN group policies to enforce security settings, access control, and session parameters for different user groups or roles. This includes defining encryption methods, access control lists (ACLs), and split tunneling policies.
Set Up VPN Tunnel: Configure the VPN tunnel parameters, including encryption algorithms, IKE (Internet Key Exchange) policies, and phase 1/phase 2 settings to establish secure communication between the remote clients and the ASA.
Deploy AnyConnect Profiles: Deploy AnyConnect profiles to customize client settings and provide users with a seamless VPN experience. Profiles can include VPN server addresses, certificate authentication settings, and automatic connection options.
Testing and Monitoring: After configuring the ASA VPN for AnyConnect access, thoroughly test the connectivity and functionality of the VPN solution. Monitor VPN traffic, authentication logs, and security events to ensure compliance and detect any anomalies or issues.
By following these steps, organizations can effectively configure an ASA VPN for AnyConnect access, providing secure remote connectivity for employees, contractors, and partners while safeguarding sensitive data and network resources.
0 notes
Text
Docker Online Training Hyderabad | Visualpath
Kubernetes Authentication and Authorization
Introduction:
Kubernetes authentication and authorization mechanisms play a critical role in safeguarding clusters against unauthorized access and protecting sensitive workloads and data. - Docker and Kubernetes Training
Authentication in Kubernetes:
Authentication is the process of verifying the identity of users or entities attempting to access a Kubernetes cluster. Kubernetes supports various authentication methods, each catering to different use cases and deployment scenarios:
Client Certificates: Kubernetes can authenticate users based on client certificates signed by a trusted Certificate Authority (CA). This method is commonly used in production environments, where users authenticate using X.509 client certificates issued by the cluster's CA. - Kubernetes Online Training
Static Tokens: Kubernetes allows administrators to create static bearer tokens associated with specific users or service accounts. While convenient for testing and development, static tokens pose security risks if not managed properly and are not recommended for production use.
Service Account Tokens: Kubernetes automatically creates service accounts for pods running within the cluster. Service account tokens, mounted as secrets within pods, enable applications to authenticate with the Kubernetes API server and access cluster resources.
External Identity Providers: Kubernetes can integrate with external identity providers (e.g., LDAP, OAuth, OpenID Connect) for user authentication. This approach enables centralized identity management and single sign-on (SSO) capabilities across multiple Kubernetes clusters. - Docker Online Training
Implementing Authorization Policies:
Authorization, also known as access control, determines the actions users or entities are allowed to perform within a Kubernetes cluster. Kubernetes employs Role-Based Access Control (RBAC) as its primary authorization mechanism, allowing administrators to define granular access policies based on roles and role bindings:
Roles: A role defines a set of permissions (e.g., create, read, update, delete) for a specific set of resources within a Kubernetes namespace. Roles are scoped to a namespace and can be created using YAML manifest files.
Role Bindings: Role bindings associate roles with users, groups, or service accounts, granting them the permissions defined by the corresponding roles. Kubernetes supports both RoleBindings (for assigning roles within a namespace) and ClusterRoleBindings (for assigning roles across the entire cluster). - Kubernetes Training Hyderabad
Cluster Roles: In addition to namespace-scoped roles, Kubernetes supports cluster-wide roles called ClusterRoles. ClusterRoles enable administrators to define global access policies that apply across all namespaces within the cluster.
Best Practices for Kubernetes Authentication and Authorization:
Implement RBAC: Utilize Kubernetes RBAC to define fine-grained access controls based on the principle of least privilege. Regularly review and audit role definitions and role bindings to ensure they align with security policies and least privilege principles.
Leverage Service Accounts: Use Kubernetes service accounts to authenticate and authorize applications and workloads running within the cluster. Avoid using static bearer tokens or overly permissive access controls for service accounts. - Docker and Kubernetes Online Training
Enable Network Policies: Implement Kubernetes Network Policies to control traffic flow between pods and enforce network segmentation. Network policies augment RBAC by restricting network communication based on pod labels, namespaces, and other attributes.
Integrate with Identity Providers: Integrate Kubernetes with external identity providers to enable centralized authentication and SSO across multiple clusters. Leverage standard protocols like OAuth and OpenID Connect for seamless integration with existing identity management systems.
Regularly Rotate Secrets: Rotate client certificates, bearer tokens, and other authentication credentials regularly to mitigate the risk of unauthorized access due to compromised credentials or expired certificates.
Conclusion:
Authentication and authorization are foundational pillars of Kubernetes security, ensuring that only authorized users and workloads can access and interact with cluster resources.
Visualpath is the Leading and Best Institute for learning Docker And Kubernetes Online in Ameerpet, Hyderabad. We provide Docker Online Training Course, you will get the best course at an affordable cost.
Attend Free Demo
Call on - +91-9989971070.
Visit : https://www.visualpath.in/DevOps-docker-kubernetes-training.html
WhatsApp : https://www.whatsapp.com/catalog/919989971070/
#KubernetesTrainingHyderabad#KubernetesOnlineTraining#DockerandKubernetesTraining#DockerOnlineTraining#DockerTraininginHyderabad#DockerandKubernetesOnlineTraining#KubernetesTraininginAmeerpet
0 notes
Text
Mastering Access Control: The Art of Flexible User Administration
"Flexible user administration" typically refers to the capability of a system, software application, or platform to adapt and customize user management functionalities based on specific requirements. It involves providing administrators with versatile tools and options to control user access, permissions, and other related settings. Here are some key aspects associated with flexible user administration:
User Roles and Permissions: Systems with flexible user administration often allow administrators to define various user roles, each with its set of permissions. This enables fine-grained control over what actions different users can perform within the system.
Customizable User Profiles: The ability to create and customize user profiles allows administrators to tailor the user experience based on individual or group needs. This may include setting preferences, defining access levels, and configuring other user-specific settings.
Access Control Lists (ACLs): Flexible user administration often involves the use of Access Control Lists, which are lists of permissions attached to an object (such as a file, folder, or system resource). Administrators can configure ACLs to control who can access or manipulate specific resources.
User Registration and Onboarding: Systems with flexible user administration provide options for customizing the user registration and onboarding processes. This may involve setting up approval workflows, verifying user information, and managing the registration experience.
Password Policies and Security Measures: Administrators can define and enforce password policies, such as minimum length, complexity requirements, and expiration periods. Additionally, flexible user administration includes options for implementing additional security measures, such as multi-factor authentication.
User Delegation: Delegating administrative tasks to specific users or roles is a key feature of flexible user administration. This ensures that different responsibilities can be distributed among team members while maintaining control over the overall system.
Integration with Identity Providers: Systems with flexible user administration often support integration with external identity providers, such as LDAP (Lightweight Directory Access Protocol) or OAuth/OpenID providers. This allows for centralized user management and authentication.
Audit Trails and Reporting: To maintain accountability and compliance, flexible user administration includes features like audit trails and reporting. These tools allow administrators to track user activities, changes to permissions, and other relevant events.
In summary, flexible user administration is about providing administrators with the tools and options they need to adapt user management processes to the specific requirements of their organization or system. It enhances the overall manageability, security, and customization of user-related functionalities within a given platform or application.
#flexibleuseradministration #connectivity #hosting
0 notes
Text
Master Identity Management with Okta Certified Professional Training
In today’s digital-first enterprise landscape, identity and access management (IAM) has become a cornerstone of secure IT operations. Whether you're an IT admin looking to upskill or a cybersecurity enthusiast preparing to transition into cloud security, Okta Certified Professional Training offers a strategic pathway to mastering IAM and advancing your career.
Why Learn Okta for Identity and Access Management?
With organizations rapidly moving to cloud-based infrastructures, the demand for robust IAM solutions like Okta has surged. According to industry reports, IAM-related roles have grown by 38% over the past three years, highlighting the growing need for professionals skilled in managing secure identity frameworks.
The Okta Certified Professional course is designed to bridge that skills gap—offering real-world use cases, hands-on labs, and a certification-based curriculum to equip you with the tools to secure and streamline user identity in enterprise environments.
What You’ll Learn in the Okta IAM Training
This foundational course provides a deep dive into the Okta platform, making it ideal for System Administrators, Security Analysts, and IT professionals responsible for configuring and managing user identities.
Key learning areas include:
User Lifecycle Management: Create and manage users, groups, and rules.
Secure Access Controls: Configure password and sign-on policies, implement MFA.
Directory Integration: Connect with Active Directory and LDAP.
SSO & SAML Authentication: Set up secure Single Sign-On for applications.
Universal Directory Mastery: Map and manage user profile attributes effectively.
You'll also gain access to lab environments and study materials for 30 days post-training, reinforcing your learning through continued practice.
Key Benefits of the Training
✅ Hands-on IAM Scenarios: Apply what you learn in simulated real-time environments.
✅ Expert-Led Guidance: Learn from certified Okta training partners.
✅ Career Advancement: Aligns with roles in IAM, cloud security, and enterprise IT.
✅ Flexible Scheduling: Study on your terms with 24/7 support and one-on-one doubt clearing.
✅ Certification Preparation: Get fully prepared for the Okta Certified Professional exam, recognized by over 70% of cloud-adopting organizations.
Who Should Enroll?
This training is ideal for:
IT professionals seeking specialization in IAM.
Security analysts shifting toward cloud security.
Cloud architects integrating Okta into enterprise systems.
Corporate IT teams implementing SSO and MFA.
Entry-level tech professionals aiming for certification and growth.
Prerequisites
To ensure a smooth learning experience, participants should have:
A basic understanding of IT systems, networking, and cybersecurity.
Familiarity with identity management tools like Active Directory (recommended).
Prior exposure to cloud platforms or SSO is helpful, though not mandatory.
No previous Okta certification is needed—making this course perfect for IT pros with foundational experience looking to build their IAM credentials.
Final Thoughts
If you’re aiming to specialize in identity management or future-proof your career in cloud security, Okta Certified Professional Training is your stepping stone. With expert instruction, real-world labs, and certification readiness, you’ll gain not just skills—but confidence to lead IAM initiatives in any enterprise.
🚀 Start your journey today and master the tools that secure the modern workplace.
1 note
·
View note
Text
Advanced Linux System Administration
Linux Training in Chandigarh, Advanced Linux system administration involves mastering complex tasks to maintain, optimize, and secure Linux servers. Here are key aspects of advanced Linux system administration:
Kernel Tuning: Adjusting kernel parameters and performance settings for specific workloads, such as memory management, I/O scheduling, and network configurations.
Filesystem Management: Managing filesystems, including advanced features like LVM (Logical Volume Management), RAID configurations, and optimizing filesystem performance.
Networking: Configuring advanced network settings, including VLANs, bridging, and routing. Implementing firewalls and VPNs using tools like iptables, OpenVPN, or IPsec.
User and Group Management: Managing users, groups, and permissions effectively. Implementing centralized authentication systems like LDAP or Active Directory for user management.
Security Hardening: Implementing security best practices, such as configuring SELinux/AppArmor, conducting regular security audits, and staying updated on vulnerabilities.
Backup and Recovery: Developing comprehensive backup strategies, including full and incremental backups, and creating disaster recovery plans.
Monitoring and Logging: Using tools like Nagios, Zabbix, or Prometheus for monitoring, and configuring centralized logging systems with ELK stack or syslog-ng.
Virtualization and Containers: Implementing virtualization using tools like KVM or Xen, and managing containers with Docker or Kubernetes for efficient resource utilization.
Performance Optimization: Profiling system performance with tools like Sar, vmstat, or perf, and optimizing system resources based on usage patterns.
Automation: Leveraging automation tools like Ansible, Puppet, or Chef to streamline configuration management and ensure consistency across servers.
High Availability: Implementing high availability solutions like clustering (Pacemaker/Corosync) or load balancing (HAProxy) for mission-critical services.
Troubleshooting: Developing advanced troubleshooting skills using diagnostic tools like strace, tcpdump, and Wireshark to pinpoint and resolve complex issues.
Patch Management: Keeping systems up to date with security patches and managing software updates efficiently.
Advanced Linux system administration requires a deep understanding of Linux internals, security principles, and a willingness to continuously learn and adapt to new technologies. It's crucial for maintaining the reliability, security, and performance of Linux servers in enterprise environments.
0 notes
Text
Real-World Applications of RHCSA and RHCE Skills
The Red Hat Certified System Administrator (RHCSA) and Red Hat Certified Engineer (RHCE) certifications are highly regarded in the IT industry. These certifications validate an individual's skills in managing and automating Red Hat Enterprise Linux environments. However, the value of these certifications extends beyond just passing exams; the skills acquired are directly applicable to various real-world scenarios in the IT domain. Let's explore some of the practical applications of RHCSA and RHCE skills.
1. Server Management and Maintenance
RHCSA:
User and Group Management: Creating, modifying, and managing user accounts and groups. This is crucial for maintaining security and organization within a server environment.
File Permissions and ACLs: Setting appropriate permissions and access control lists to protect sensitive data and ensure users have the necessary access to perform their jobs.
Service Management: Starting, stopping, enabling, and disabling services using systemctl. This is essential for maintaining the uptime and performance of services.
RHCE:
Advanced System Monitoring: Using tools like top, htop, vmstat, and iotop to monitor system performance and diagnose issues.
Network Management: Configuring and troubleshooting network interfaces, firewalls, and SELinux settings to secure and optimize network communications.
2. Automating System Administration Tasks
RHCSA:
Shell Scripting: Writing basic scripts to automate repetitive tasks, such as backups, user creation, and log rotation.
Cron Jobs: Scheduling routine tasks to run automatically at specified times, ensuring consistent system maintenance without manual intervention.
RHCE:
Ansible Automation: Utilizing Ansible for configuration management and automation. Creating playbooks to automate complex multi-tier deployments and configurations.
Automating Deployments: Streamlining the process of deploying applications and services using automated scripts and configuration management tools.
3. System Security and Compliance
RHCSA:
Security Enhancements: Implementing basic security measures such as configuring firewalls with firewalld, and managing SELinux to enforce security policies.
Auditing and Logging: Setting up and maintaining system logs to monitor and audit system activities for compliance and troubleshooting purposes.
RHCE:
Advanced Security Configurations: Applying more sophisticated security measures such as configuring advanced SELinux policies, managing TLS/SSL certificates for secure communications, and implementing secure SSH practices.
System Auditing and Reporting: Using tools like auditd to create detailed security audits and reports, ensuring systems comply with security policies and standards.
4. Troubleshooting and Problem Solving
RHCSA:
Basic Troubleshooting: Using commands like journalctl, dmesg, and systemctl to diagnose and resolve common issues related to system performance, boot processes, and service failures.
Disk Management: Managing storage with LVM (Logical Volume Management) and understanding disk usage with tools like df and du.
RHCE:
Advanced Troubleshooting: Diagnosing complex issues involving network services, storage systems, and application performance. Using advanced tools and techniques to pinpoint and resolve problems.
System Recovery: Implementing disaster recovery plans, including restoring from backups, repairing boot issues, and recovering corrupted file systems.
5. Managing Enterprise Environments
RHCSA:
Package Management: Installing, updating, and managing software packages using yum or dnf, ensuring that systems have the necessary software and updates.
Network Configuration: Setting up and managing basic network configurations, including IP addresses, DNS settings, and hostname configurations.
RHCE:
Centralized Authentication: Setting up and managing centralized authentication services such as LDAP, Kerberos, and integrating with Active Directory.
Clustering and High Availability: Configuring and managing Red Hat High Availability Clustering to ensure critical services are always available.
6. DevOps and Continuous Integration/Continuous Deployment (CI/CD)
RHCSA:
Version Control Systems: Basic knowledge of version control systems like Git, which is fundamental for managing code and configuration files.
Containerization: Introduction to containerization concepts using tools like Docker.
RHCE:
CI/CD Pipelines: Setting up and managing CI/CD pipelines using tools like Jenkins, GitLab CI, or Red Hat OpenShift, enabling automated testing, integration, and deployment of applications.
Advanced Container Management: Managing and orchestrating containers using Kubernetes and Red Hat OpenShift, ensuring scalable and reliable deployment of containerized applications.
Conclusion
The skills acquired through RHCSA and RHCE certifications are not just theoretical but have direct, practical applications in the real world. Whether it's managing and securing servers, automating administrative tasks, or setting up robust enterprise environments, these certifications equip IT professionals with the knowledge and tools necessary to excel in their careers. By applying these skills, professionals can ensure efficient, secure, and high-performing IT operations, ultimately driving organizational success.
For more details click www.qcsdclabs.com
#redhatcourses#information technology#containerorchestration#kubernetes#docker#linux#container#qcsdclabs#rhcsa#rhce#devops#ansibleautomation
1 note
·
View note
Text
Active Directory PowerShell commands cheat sheet
Get users in a group in descending order; recursively qualify all the nested groups
Get-ADGroupMember - Recursive - Identity <groupname> | Select-ExpandProperty SamAccountName | Sort-Object
Get information about a user from Active Directory and store it in a text file named info.txt
Get-ADUser -Identity <username format for organization> -Properties * > info.txt
Get information about a user from Active Directory based on a filter
Get-ADUser -Properties * -Filter “(city -eq ‘New York’) | Select-Object -last 10 -Property samAccountName, Modified, Enabled
Get information about a user from Active Directory in a specific OU
Get-ADUser -SearchBase “OU=abc,DC=test,DC=com” | Select-Object -last 10 -Property samAccountName, Modified, Enabled
Get information about a user from Active Directory using LDAP dialect
Get-ADUser -LDAPFilter ‘(&(objectCategory=User)([email protected]));’
1 note
·
View note
Text
Actualizar openSUSE 15.2 a openSUSE 15.3

Actualizar openSUSE 15.2 a openSUSE 15.3 de manera sencilla. No vamos a hablar de las bondades de esta magnífica distribución Linux, pues muchos ya sabéis que es una de mis favoritas. OpenSUSE es una distribución diferente, potente, poderosa, fácil de usar, versátil y, con un funcionamiento como servidor empresarial que pocos le hacen sombra. La forma de operar de openSUSE no hace que su actualización, sea tan simple como en otras distribuciones linux, sobre todos las basadas en deb, como Ubuntu, Linux Mint, etc. Consciente de que existen muchas dudas y errores al respecto, hemos realizado una instalación limpia de openSUSE 15.2 con Ext4 y, la hemos actualizado a openSUSE 15.3 con un resultado satisfactorio. En este artículo verás como lo hemos hecho, de forma rápida y sencilla.

Actualizar openSUSE 15.2 a openSUSE 15.3 de forma sencilla
Actualizar openSUSE 15.2 a openSUSE 15.3
Antes de comenzar, verificamos que efectivamente tenemos instalada la versión 15.2. cat /etc/*release Ejemplo... localhost:~ # cat /etc/*release NAME="openSUSE Leap" VERSION="15.2" ID="opensuse-leap" ID_LIKE="suse opensuse" VERSION_ID="15.2" PRETTY_NAME="openSUSE Leap 15.2" ANSI_COLOR="0;32" CPE_NAME="cpe:/o:opensuse:leap:15.2" BUG_REPORT_URL="https://bugs.opensuse.org" HOME_URL="https://www.opensuse.org/" localhost:~ # Lo primero y muy importante, es deshabilitar los repositorios que no sean oficiales. Para ello desde YaST, accedemos a YaST Software Repositories.

Acceder a YaST Software Repositories Una vez en YaST Software Repositories, deshabilita los repositorios que no sean oficiales. Deja habilitados, solo los que ves en la siguiente imagen.
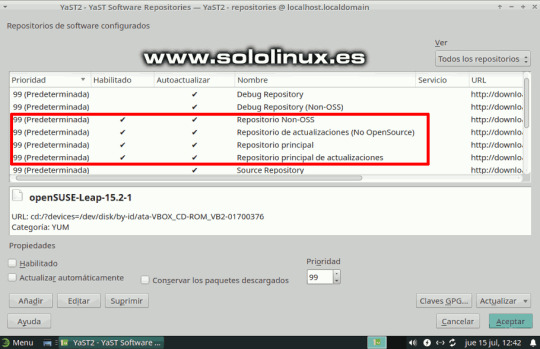
Repositorios habilitados de openSUSE Bien, una vez deshabilitados los repositorios no oficiales salimos de YaST. Abre la terminal y accede como superusuario. sudo su Ahora refrescamos los repositorios habilitados y actualizamos. zypper ref zypper up Verás un resultado similar al siguiente. localhost:~ # zypper ref Repository 'Repositorio Non-OSS' is up to date. Repository 'Repositorio principal' is up to date. Retrieving repository 'Repositorio principal de actualizaciones' metadata Building repository 'Repositorio principal de actualizaciones' cache ..... Repository 'Repositorio de actualizaciones (No OpenSource)' is up to date. All repositories have been refreshed. localhost:~ # zypper up Building repository 'Repositorio Non-OSS' cache ........................ Building repository 'Repositorio principal' cache ...................... Building repository 'Repositorio principal de actualizaciones' cache ... Building repository 'Repositorio de actualizaciones (No OpenSource)' cac Loading repository data... Reading installed packages... Nothing to do. Bueno, llego la hora de la verdad. Debes copiar la siguiente secuencia de comandos al completo y, pegarla en tu terminal. Lo que hacemos es modificar la versión 15.2 por la 15.3. Recuerda... copia todo completo y pégalo, si lo haces línea por línea no funcionara correctamente. files="$(zypper lr -u | awk -F'|' '$4 ~ /Yes/ { gsub (" ", "", $2); r="/etc/zypp/repos.d/"$3".repo"; print r }')" for f in $files do echo "Backup of $f saved to /root/ before patching it up ..." cp -f "$f" /root/ sed -i 's+/leap/15.2+/leap/$releasever+' "$f" sed -i 's+15.2.1+15.3+' "$f" sed -i 's+15.2+15.3+' "$f" done Debe quedar como la siguiente imagen.

Migrar openSUSE 15.2 a openSUSE 15.3 Refrescamos los repositorios, indicando que sean los de la nueva versión 15.3. zypper --releasever=15.3 ref Ejemplo... zypper --releasever=15.3 ref localhost:~ # zypper --releasever=15.3 ref Warning: Enforced setting: $releasever=15.3 Retrieving repository 'Repositorio Non-OSS' metadata ..................... Building repository 'Repositorio Non-OSS' cache .......................... Retrieving repository 'Repositorio principal' metadata ................... Building repository 'Repositorio principal' cache ........................ Retrieving repository 'Repositorio principal de actualizaciones' metadata Building repository 'Repositorio principal de actualizaciones' cache ..... Retrieving repository 'Repositorio de actualizaciones (No OpenSource)' met Building repository 'Repositorio de actualizaciones (No OpenSource)' cache All repositories have been refreshed. localhost:~ # Llagó el momento de la actualización real. Te recomiendo ser paciente, puede demorar hasta 45 minutos. zypper --releasever=15.3 dup Ejemplo... localhost:~ # zypper --releasever=15.3 dup Warning: Enforced setting: $releasever=15.3 Retrieving repository 'Repositorio Non-OSS' metadata ..................... Building repository 'Repositorio Non-OSS' cache .......................... Retrieving repository 'Repositorio principal' metadata ................... Building repository 'Repositorio principal' cache ............................................ Retrieving repository 'Repositorio principal de actualizaciones' metadata .................... Building repository 'Repositorio principal de actualizaciones' cache ......................... Retrieving repository 'Repositorio de actualizaciones (No OpenSource)' metadata .............. Building repository 'Repositorio de actualizaciones (No OpenSource)' cache ................... Loading repository data... Reading installed packages... Warning: You are about to do a distribution upgrade with all enabled repositories. Make sure these repositories are compatible before you continue. See 'man zypper' for more information about this command. Computing distribution upgrade... The following 156 NEW packages are going to be installed: alsa-plugins-speexrate alsa-plugins-upmix alsa-ucm-conf coreutils-doc cryptsetup-lang dirmngr evince evince-lang evince-plugin-pdfdocument file-roller file-roller-lang glibc-lang gnome-calculator gnome-calculator-lang gnome-desktop-lang google-poppins-fonts gspell-lang gtksourceview4-lang issue-generator kernel-default-5.3.18-57.3 kernel-default-extra kernel-default-optional kernel-firmware-all kernel-firmware-amdgpu kernel-firmware-ath10k kernel-firmware-ath11k kernel-firmware-atheros kernel-firmware-bluetooth kernel-firmware-bnx2 kernel-firmware-brcm kernel-firmware-chelsio kernel-firmware-dpaa2 kernel-firmware-i915 kernel-firmware-intel kernel-firmware-iwlwifi kernel-firmware-liquidio kernel-firmware-marvell kernel-firmware-media kernel-firmware-mediatek kernel-firmware-mellanox kernel-firmware-mwifiex kernel-firmware-network kernel-firmware-nfp kernel-firmware-nvidia kernel-firmware-platform kernel-firmware-prestera kernel-firmware-qlogic kernel-firmware-radeon kernel-firmware-realtek kernel-firmware-serial kernel-firmware-sound kernel-firmware-ti kernel-firmware-ueagle kernel-firmware-usb-network kmod-bash-completion libLLVM11 libatopology2 libavcodec58_134 libavformat58_76 libavutil56_70 libblogger2 libbrotlienc1 libcbor0 libcdio19 libcrypt1 libdav1d5 libebtc0 libevdocument3-4 libevview3-3 libfido2-1 libfido2-udev libgepub-0_6-0 libgnome-desktop-3-18 libgnome-desktop-3_0-common libgspell-1-2 libgtksourceview-4-0 libgtop-2_0-11 libgtop-lang libldac2 libmfx1 libmpath0 libndr1 libnftables1 libnss_usrfiles2 libpeas-loader-python libply-boot-client5 libply-splash-core5 libply-splash-graphics5 libply5 libre2-9 libswresample3_9 libtextstyle0 liburing1 libyui-ncurses-pkg15 libyui-ncurses15 libyui-qt-graph15 libyui-qt-pkg15 libyui-qt15 libyui15 login_defs man-pages-es metamail mokutil mpt-status nftables openSUSE-signkey-cert openssh-clients openssh-common openssh-server p7zip-full pam-doc pam_pwquality patterns-base-documentation patterns-base-sw_management patterns-yast-yast2_desktop perl-TermReadLine-Gnu perl-core-DB_File pipewire-lang postfix-ldap procinfo procmail python3-brotlipy python3-cairo python3-nftables python3-smbc rpm-config-SUSE ruby2.5-rubygem-mini_portile2 ruby2.5-rubygem-nokogiri setserial sharutils sharutils-lang spax star star-rmt sudo-plugin-python system-group-audit system-group-kvm systemd-default-settings systemd-default-settings-branding-openSUSE systemd-doc systemd-lang typelib-1_0-Libxfce4ui-2_0 typelib-1_0-Libxfce4util-1_0 typelib-1_0-Xfconf-0 virtualbox-kmp-default-6.1.22_k5.3.18_59.5-lp153.2.3.2 vlan xreader-plugin-comicsdocument xreader-plugin-djvudocument xreader-plugin-dvidocument xreader-plugin-epubdocument xreader-plugin-pdfdocument xreader-plugin-pixbufdocument xreader-plugin-psdocument xreader-plugin-tiffdocument xreader-plugin-xpsdocument yast2-trans-en The following 3 NEW patterns are going to be installed: documentation sw_management yast2_desktop The following NEW product is going to be installed: "openSUSE Leap 15.3" The following 22 packages are going to be REMOVED: exo-branding-openSUSE exo-helpers hardlink kernel-firmware kmod-compat libexo-1-0 libndr0 libre2-6 libxfce4panel-1_0-4 libxfce4ui-1-0 libyui-ncurses-pkg11 libyui-qt-pkg11 patterns-base-apparmor_opt patterns-base-enhanced_base_opt patterns-base-x11_opt python3-pycairo python3-pysmbc systemd-bash-completion typelib-1_0-libxfce4util-1_0 xfce4-statusnotifier-plugin xfce4-statusnotifier-plugin-lang xreader-backends --------------etc............
Descargar y actualizar los nuevos paquetes Al concluir todo el proceso, te pregunta si quieres reiniciar el sistema. Responde "Y". 1762 packages to upgrade, 192 to downgrade, 156 new, 22 to remove, 1667 to change vendor. Overall download size: 1.59 GiB. Already cached: 0 B. After the operation, additional 308.9 MiB will be used. Note: System reboot required. Continue? (y): Sorpresa!!!, al iniciar el sistema ya vemos que arranca openSUSE 15.3.
Iniciar openSUSE 15.3 Verificamos desde nuestra consola / terminal. cat /etc/*release El resultado es un exito. localhost:~ # cat /etc/*release NAME="openSUSE Leap" VERSION="15.3" ID="opensuse-leap" ID_LIKE="suse opensuse" VERSION_ID="15.3" PRETTY_NAME="openSUSE Leap 15.3" ANSI_COLOR="0;32" CPE_NAME="cpe:/o:opensuse:leap:15.3" BUG_REPORT_URL="https://bugs.opensuse.org" HOME_URL="https://www.opensuse.org/" localhost:~ # Ahora solo te falta modificar los repositorios no oficiales en YaST Software Repositories (aunque se hayan modificado automáticamente, debes verificarlos de forma manual). Una vez termines el proceso, los habilitas y actualizas de nuevo para concluir todo el proceso. sudo zypper ref sudo zypper up Canales de Telegram: Canal SoloLinux – Canal SoloWordpress Espero que este artículo te sea de utilidad, puedes ayudarnos a mantener el servidor con una donación (paypal), o también colaborar con el simple gesto de compartir nuestros artículos en tu sitio web, blog, foro o redes sociales. Chat de SoloLinux en Telegram Read the full article
#deb#distribucionlinux#IniciaropenSUSE15.3#opensuse#openSUSE15.2#openSUSE15.2aopenSUSE15.3#openSUSE15.2conExt4#openSUSE15.3#servidorempresarial#YaST#YaSTSoftwareRepositories
1 note
·
View note